Embarking on a journey to understand back-end development might seem daunting, but it’s actually a fascinating world where the magic of websites and applications truly happens. Think of it as the engine room of the internet – the place where data is stored, processed, and served up to your screens. This guide aims to demystify this area, breaking down complex concepts into easy-to-grasp explanations and practical examples, making your entry into the back-end world smooth and enjoyable.
This exploration will cover essential topics, starting with the fundamentals like what back-end development actually
-is* and the core technologies that power it. We’ll delve into databases, the heart of data storage, and explore server-side programming, where the logic and functionality of applications reside. From API development to version control, deployment, security, testing, and even scaling, we’ll equip you with a foundational understanding of the key elements.
Consider this your launchpad into a dynamic and crucial field of software development.
Introduction to Back-End Development
Back-end development is the engine room of the internet. It’s the part of a website or application that users don’t directly see or interact with. Think of it as the behind-the-scenes operations that make everything work smoothly, from storing information to processing user requests. This is where the magic happens, ensuring the front-end (what you see) functions correctly.
What Back-End Development Encompasses
Back-end development involves building and maintaining the server-side components of a web application or mobile app. It’s responsible for managing data, handling user authentication, and ensuring the application runs efficiently. This work is crucial for delivering a seamless user experience.
Common Back-End Tasks
The back-end handles a variety of essential tasks. These tasks are critical for the functionality and security of any application.
- Database Management: This involves designing, implementing, and maintaining databases to store and retrieve data. Databases organize information, making it accessible and manageable. For example, when you create an account on a social media platform, your username, password, and profile information are stored in a database.
- Server-Side Logic: This refers to the code that runs on the server to process requests, perform calculations, and generate responses. This logic handles everything from processing form submissions to displaying dynamic content. Imagine you’re buying something online; the server-side logic processes your order, calculates the total cost, and updates inventory.
- API Development: APIs (Application Programming Interfaces) are sets of rules and specifications that software programs can use to communicate with each other. Back-end developers create APIs that allow the front-end to access data and functionality from the server. Consider a weather app; it uses an API to fetch weather data from a remote server and display it to the user.
- Security Implementation: Back-end developers are responsible for implementing security measures to protect data and prevent unauthorized access. This includes things like user authentication, data encryption, and protection against common vulnerabilities. This is crucial for protecting sensitive user information, like credit card details.
Importance of Back-End Development
Back-end development is the backbone of modern web applications and mobile apps. It’s what allows them to function, store data, and interact with users. Without a robust back-end, applications would be unable to provide any real functionality.
- Data Storage and Retrieval: Back-end development ensures that data is stored securely and efficiently, allowing users to access and manage information. E-commerce platforms, for example, rely heavily on back-end systems to store product information, manage inventory, and process transactions.
- Scalability and Performance: A well-designed back-end can handle a large volume of traffic and data, ensuring the application remains responsive and performs well even under heavy load. Popular social media platforms like Facebook and Instagram have massive back-ends that are designed to handle millions of users and constant data updates.
- User Authentication and Authorization: Back-end development is responsible for verifying user identities and controlling access to resources. This is essential for protecting user data and ensuring that only authorized users can perform certain actions. Consider a banking app; the back-end verifies your credentials and allows you to access your account information.
- Integration with Third-Party Services: Back-end developers integrate applications with external services, such as payment gateways, social media platforms, and other APIs. This integration allows applications to provide a wider range of features and functionality. For instance, a food delivery app uses back-end logic to integrate with payment gateways for processing orders.
Core Technologies and Languages
Back-end development relies on a variety of technologies to handle server-side logic, data management, and the overall functionality of a web application. Understanding these core technologies and languages is essential for building robust and scalable back-end systems. This section explores the key programming languages, database systems, and web servers that form the foundation of back-end development.
Programming Languages in Back-End Development
Programming languages are the tools that developers use to write the instructions that the back-end server will execute. Different languages offer various strengths, making them suitable for different types of projects.
- Python: Python is a versatile, high-level language known for its readability and extensive libraries. Its clear syntax makes it relatively easy to learn, and its frameworks like Django and Flask simplify web development.
Python’s popularity stems from its use in various domains, including:
- Web Development: Django and Flask are popular frameworks.
- Data Science and Machine Learning: Libraries like Pandas, NumPy, and Scikit-learn.
- Automation and Scripting: Useful for automating tasks.
Python is particularly well-suited for projects requiring rapid development, data analysis, and complex logic.
- Java: Java is a robust, object-oriented language known for its platform independence (write once, run anywhere). It’s widely used in enterprise-level applications due to its scalability and security features. Frameworks like Spring and Jakarta EE (formerly Java EE) provide powerful tools for building complex back-end systems.
Java’s strengths include:- Scalability: Suitable for large-scale applications.
- Security: Strong security features.
- Performance: Optimized for performance.
Java is often chosen for applications that demand high performance, reliability, and security, such as financial systems and large e-commerce platforms.
- Node.js: Node.js is a JavaScript runtime environment that allows developers to run JavaScript on the server-side. It uses an event-driven, non-blocking I/O model, making it highly efficient for handling concurrent requests. Frameworks like Express.js simplify the development of web applications and APIs.
Node.js’s advantages include:- JavaScript Everywhere: Uses the same language for both front-end and back-end.
- Performance: Efficient handling of concurrent requests.
- Large Ecosystem: Extensive package ecosystem (npm).
Node.js is a popular choice for building real-time applications (e.g., chat applications), APIs, and applications that require high performance and scalability.
Database Systems: SQL vs. NoSQL
Databases are essential for storing and managing the data that back-end applications rely on. Two primary types of database systems are SQL (relational) and NoSQL (non-relational).
- SQL (Relational Databases): SQL databases organize data into tables with predefined schemas. They use Structured Query Language (SQL) for querying and manipulating data.
Key characteristics include:
- Structured Data: Data is organized in tables with rows and columns.
- ACID Properties: Transactions follow Atomicity, Consistency, Isolation, and Durability principles.
- Schema: Requires a predefined schema.
Examples include MySQL, PostgreSQL, and Oracle. SQL databases are ideal for applications that require data integrity, complex queries, and structured data, such as financial systems and e-commerce platforms.
- NoSQL (Non-Relational Databases): NoSQL databases offer flexible data models and are designed to handle large volumes of unstructured or semi-structured data. They often prioritize scalability and performance over strict data consistency.
Common types include:- Document Databases: Store data in JSON-like documents (e.g., MongoDB).
- Key-Value Stores: Store data as key-value pairs (e.g., Redis).
- Graph Databases: Store data as nodes and relationships (e.g., Neo4j).
NoSQL databases are well-suited for applications that require high scalability, flexibility, and handle large volumes of data, such as social media platforms, content management systems, and real-time analytics.
- Comparison:
Feature SQL NoSQL Data Model Relational (tables, rows, columns) Various (document, key-value, graph) Schema Predefined Flexible/Schema-less Data Consistency Strong (ACID) Eventual/Relaxed Scalability Vertical (scaling up) Horizontal (scaling out) Querying Complex SQL queries Varies by database type Choosing between SQL and NoSQL depends on the specific requirements of the application, including data structure, consistency needs, and scalability requirements.
Web Servers and Their Interaction with Back-End Code
Web servers are software applications that handle requests from clients (e.g., web browsers) and serve web content. They act as intermediaries between the client and the back-end application.
- Function of Web Servers:
Web servers primarily serve static content (HTML, CSS, JavaScript, images) and forward dynamic requests to the back-end application server.Key functions include:
- Handling HTTP Requests: Receiving and processing HTTP requests.
- Serving Static Content: Delivering static files.
- Reverse Proxying: Forwarding requests to back-end servers.
- Load Balancing: Distributing traffic across multiple servers.
- Examples of Web Servers:
- Apache HTTP Server: A widely used open-source web server known for its flexibility and extensive modules.
- Nginx: A high-performance web server and reverse proxy server, often used for its efficiency in handling concurrent connections and serving static content.
- Interaction with Back-End Code: When a client requests a dynamic resource, the web server forwards the request to the back-end application server (e.g., a server running Python/Django, Java/Spring, or Node.js/Express). The application server processes the request, interacts with the database, and generates the response. The web server then receives the response from the application server and sends it back to the client.
The typical workflow involves:
- Client sends an HTTP request to the web server.
- Web server forwards the request to the application server.
- Application server processes the request, potentially interacting with a database.
- Application server generates a response (e.g., HTML, JSON).
- Web server receives the response.
- Web server sends the response to the client.
- Load Balancing and Scalability: Web servers can be configured to distribute traffic across multiple application servers, improving performance and availability. This load balancing helps to handle increased traffic and ensures the application remains responsive even during peak loads.
For example, a website experiencing a surge in traffic might use Nginx as a load balancer to distribute requests across multiple back-end servers, preventing any single server from becoming overwhelmed.
Understanding Databases
Databases are fundamental to back-end development, acting as the central repositories for storing, organizing, and managing the data that powers applications. They are essential for everything from simple websites to complex enterprise systems. Understanding how databases work is crucial for any aspiring back-end developer.
Databases and Data Storage
A database is essentially an organized collection of structured information, or data, typically stored electronically in a computer system. Databases are designed to efficiently store, retrieve, and manage large amounts of data. They provide mechanisms for data integrity, security, and concurrency control, ensuring that data remains accurate and consistent even when accessed by multiple users or applications simultaneously.Databases employ various storage models, but the most common is the relational database model.
This model organizes data into tables, with rows representing individual records and columns representing different attributes of those records. This structured approach allows for efficient querying and manipulation of data.
Relational Database Structure
Relational databases are structured around the concept of tables, columns, and relationships. This structure provides a powerful and flexible way to organize and manage data.
- Tables: Tables are the fundamental building blocks of a relational database. Each table represents a specific entity, such as “Customers,” “Products,” or “Orders.” Each table is composed of rows and columns.
- Columns: Columns define the attributes of the data stored in a table. Each column has a specific data type, such as text, numbers, dates, or boolean values. For example, in a “Customers” table, columns might include “CustomerID,” “FirstName,” “LastName,” “Email,” and “PhoneNumber.”
- Rows (Records): Rows represent individual instances of the entity represented by the table. Each row contains values for all the columns defined in the table. For example, a row in the “Customers” table would represent a single customer and would contain their specific information in the respective columns.
- Relationships: Relationships define how different tables are connected. These relationships are established through the use of foreign keys, which link columns in one table to the primary key of another table. There are three main types of relationships:
- One-to-one: Each record in the first table is related to only one record in the second table, and vice versa.
- One-to-many: One record in the first table can be related to many records in the second table, but each record in the second table is related to only one record in the first table.
- Many-to-many: Many records in the first table can be related to many records in the second table. This is typically implemented using a “junction table” or “linking table.”
E-commerce Platform Database Schema Example
Designing a database schema involves defining the tables, columns, data types, and relationships needed to store and manage the data for a specific application. Here’s a simplified example of a database schema for an e-commerce platform, using a responsive three-column HTML table. This example Artikels the core tables and their respective columns and data types.
| Table Name | Columns | Data Types |
|---|---|---|
| Customers | CustomerID, FirstName, LastName, Email, Password, Address, City, State, ZipCode, PhoneNumber | INT (Primary Key), VARCHAR, VARCHAR, VARCHAR, VARCHAR, VARCHAR, VARCHAR, VARCHAR, VARCHAR, VARCHAR |
| Products | ProductID, ProductName, Description, Price, ImageURL, CategoryID | INT (Primary Key), VARCHAR, TEXT, DECIMAL, VARCHAR, INT (Foreign Key) |
| Categories | CategoryID, CategoryName, Description | INT (Primary Key), VARCHAR, TEXT |
| Orders | OrderID, CustomerID, OrderDate, TotalAmount, ShippingAddress, City, State, ZipCode | INT (Primary Key), INT (Foreign Key), DATE, DECIMAL, VARCHAR, VARCHAR, VARCHAR, VARCHAR |
| OrderItems | OrderItemID, OrderID, ProductID, Quantity, Price | INT (Primary Key), INT (Foreign Key), INT (Foreign Key), INT, DECIMAL |
This example illustrates how data is structured and related within a relational database. The relationships between tables, such as the connection between “Orders” and “Customers” via the `CustomerID`, enable efficient retrieval and management of data. This schema provides a foundation for storing customer information, product details, order information, and more, which is essential for an e-commerce platform.
Server-Side Programming Fundamentals
Server-side programming forms the backbone of web applications, handling the logic and data that users interact with. It’s the engine that powers dynamic websites, processing requests, managing information, and delivering content. Understanding these fundamentals is crucial for any aspiring back-end developer.
Basic Concepts of Server-Side Programming
Server-side programming relies on core programming concepts to function effectively. These building blocks enable developers to create complex applications.
- Variables: Variables are named storage locations that hold data. They are essential for storing and manipulating information within a program. Different data types can be assigned to variables.
- Data Types: Data types define the kind of value a variable can hold. Common data types include:
- Integers: Whole numbers (e.g., 1, 10, -5).
- Floating-point numbers: Numbers with decimal points (e.g., 3.14, -2.5).
- Strings: Sequences of characters (e.g., “Hello”, “Back-end”).
- Booleans: Represents truth values (e.g., True, False).
- Control Structures: Control structures determine the flow of execution in a program. They allow developers to make decisions and repeat actions based on certain conditions.
- Conditional Statements (if/else): Execute different blocks of code based on a condition.
- Loops (for/while): Repeat a block of code multiple times.
Handling User Input and Output in Python
Python is a popular language for back-end development. This section provides a Python code snippet to demonstrate how to handle user input and generate output on the server-side. This example simulates a simple server interaction.
The following code receives user input (a name) and generates a personalized greeting:
# Get user input
user_name = input("Enter your name: ")
# Generate a greeting
greeting = "Hello, " + user_name + "! Welcome to our server."
# Print the greeting to the server's output (simulating sending it back to the client)
print(greeting)
Explanation:
- The `input()` function prompts the user to enter their name.
- The entered name is stored in the `user_name` variable.
- A greeting message is created by concatenating the name with a welcome message.
- The `print()` function displays the greeting. In a real server environment, this output would be formatted and sent back to the user’s browser as an HTML response.
Using APIs for Front-End and Back-End Communication
APIs (Application Programming Interfaces) are fundamental for enabling communication between the front-end (user interface) and the back-end (server). APIs define how different software components interact with each other. This allows the front-end to request data, send data, and perform actions on the back-end.
How APIs work:
- Request: The front-end sends a request to the back-end API. This request typically includes the type of action to perform (e.g., retrieve data, create data), and any necessary data. Requests are often made using HTTP methods such as GET (retrieve data), POST (create data), PUT (update data), and DELETE (delete data).
- Processing: The back-end receives the request, processes it (e.g., queries a database, performs calculations), and prepares a response.
- Response: The back-end sends a response back to the front-end. The response typically includes data (in a format like JSON or XML) and a status code indicating the success or failure of the request (e.g., 200 OK, 404 Not Found, 500 Internal Server Error).
Example (Conceptual):
Imagine a front-end application displaying a list of blog posts. The front-end might send a GET request to the back-end API at an endpoint like `/api/posts`. The back-end, upon receiving this request, would query a database to retrieve the blog posts, format the data into JSON, and send it back to the front-end. The front-end would then use this data to dynamically display the blog posts on the webpage.
Real-world Examples:
- Social Media: When you like a post on a social media platform, the front-end sends a POST request to the back-end API to update the database.
- E-commerce: When you add an item to your cart, the front-end sends a POST request to the back-end API to store the item information in the database.
- Weather Apps: Weather applications use APIs (e.g., OpenWeatherMap API) to retrieve weather data from external sources and display it to the user.
API Development and RESTful Principles

APIs (Application Programming Interfaces) are the backbone of modern web applications, enabling different software systems to communicate and exchange data. Understanding how to design and build APIs is a crucial skill for any back-end developer. This section delves into the principles of RESTful API design, HTTP methods, endpoint examples, and the critical aspects of API security.
RESTful API Design Principles
REST (Representational State Transfer) is an architectural style for designing networked applications. It’s not a standard or a protocol, but a set of principles that, when followed, lead to more scalable, maintainable, and understandable APIs. These principles are fundamental to building effective APIs.* Statelessness: Each request from a client to a server must contain all the information needed to understand the request.
The server does not store any client context between requests. This simplifies server design and improves scalability.* Client-Server: The client and server are independent. The client is responsible for the user interface, and the server is responsible for data storage and business logic. This separation allows for independent evolution of each part.* Cacheability: Responses should be cacheable to improve performance.
The server should indicate whether a response is cacheable and for how long.* Uniform Interface: This is the most important principle. It dictates that all resources should be accessed using a consistent interface. This includes:
Resource Identification
Resources are identified by a URI (Uniform Resource Identifier).
Manipulation of Resources Through Representations
Clients manipulate resources by exchanging representations of those resources (e.g., JSON or XML).
Self-descriptive Messages
Each message contains enough information to describe how to process it.
Hypermedia as the Engine of Application State (HATEOAS)
Clients transition between application states by following links provided in the responses.* Layered System: The client may not know whether it is connected directly to the server or to an intermediary. This allows for load balancing and caching.
HTTP Methods
HTTP methods, also known as verbs, define the type of operation to be performed on a resource. RESTful APIs use these methods to provide a consistent interface for interacting with resources.* GET: Retrieves a representation of a resource. This method should be idempotent (performing the same GET request multiple times should have the same effect).* POST: Creates a new resource or submits data to be processed.
This method is not idempotent.* PUT: Updates a resource with a new representation. This method is idempotent.* DELETE: Deletes a resource. This method is idempotent.* PATCH: Partially updates a resource. This is also an idempotent operation.
API Endpoints and Functionalities
API endpoints are specific URLs that represent resources or actions. Here are some examples of API endpoints and their corresponding functionalities, demonstrating the use of HTTP methods:* /users
GET
Retrieves a list of all users.
POST
Creates a new user.
/users/id (where id is the user’s ID)
GET
Retrieves a specific user by ID.
PUT
Updates a specific user’s information.
DELETE
Deletes a specific user. – /products
GET
Retrieves a list of all products.
POST
Creates a new product.
/products/id/reviews (where id is the product’s ID)
GET
Retrieves a list of reviews for a specific product.
POST
Creates a new review for a specific product.
API Security
API security is paramount to protect sensitive data and prevent unauthorized access. There are several crucial aspects of API security, including authentication and authorization.* Authentication: Verifying the identity of the client. Common authentication methods include:
API Keys
Unique keys assigned to clients to identify them. These keys are often passed in the request headers.
JSON Web Tokens (JWT)
A standard for securely transmitting information between parties as a JSON object. JWTs are often used for stateless authentication. A JWT typically contains a header, payload, and signature.
OAuth 2.0
An open standard for authorization that allows users to grant third-party access to their resources without sharing their credentials. It involves several roles: the resource owner, the client, the authorization server, and the resource server.* Authorization: Determining whether an authenticated client has permission to access a specific resource or perform a specific action. This often involves assigning roles and permissions to users.
Role-Based Access Control (RBAC)
Users are assigned roles, and each role has specific permissions. For example, an “administrator” role might have permission to create, read, update, and delete users, while a “user” role might only have permission to read their own profile.
Access Control Lists (ACLs)
Fine-grained control over resource access, where each resource has a list of users or roles and their permitted actions.* Other Security Considerations:
Input Validation
Validating all incoming data to prevent vulnerabilities like SQL injection and cross-site scripting (XSS).
Rate Limiting
Limiting the number of requests a client can make within a certain time frame to prevent abuse and denial-of-service (DoS) attacks.
Encryption
Using HTTPS to encrypt all communication between the client and the server to protect data in transit.
Regular Security Audits
Regularly reviewing the API code and infrastructure for vulnerabilities.
Monitoring and Logging
Implementing robust monitoring and logging to detect and respond to security incidents.
Version Control with Git

Version control is an indispensable practice in back-end development, acting as a time machine for your code. It allows developers to track changes to their codebase over time, revert to previous versions if necessary, and collaborate effectively with others. Git is the most widely used version control system, offering a robust and flexible way to manage code changes.
Purpose of Version Control Systems and Git
Version control systems like Git serve several crucial purposes in software development. They enable developers to track changes, collaborate effectively, and maintain a history of their codebase.
- Tracking Changes: Every modification to the code is recorded, allowing developers to see who made what changes and when. This detailed history is invaluable for understanding the evolution of the project.
- Collaboration: Multiple developers can work on the same project simultaneously without overwriting each other’s work. Git provides tools for merging changes and resolving conflicts.
- Reverting to Previous Versions: If a bug is introduced or a feature breaks the application, developers can easily revert to a previous, working version of the code. This rollback capability is critical for maintaining stability.
- Experimentation and Branching: Git allows developers to create branches, which are independent lines of development. This enables experimentation with new features or bug fixes without affecting the main codebase.
- Code Backup and Disaster Recovery: Git repositories can be hosted remotely (e.g., on GitHub, GitLab, Bitbucket), providing a backup of the code and enabling recovery in case of local data loss.
Basic Git Commands
Understanding the fundamental Git commands is essential for effective version control. These commands allow developers to create repositories, track changes, and manage branches.
- Creating a Repository: The first step is to initialize a Git repository in your project directory. This creates a hidden `.git` folder that stores all the version control information.
git init - Committing Changes: After making changes to your code, you need to stage them and then commit them to the repository. Staging specifies which changes will be included in the next commit. Committing saves the changes with a descriptive message.
git add .(stages all changed files)git commit -m "Descriptive commit message" - Branching: Branches allow developers to work on features or bug fixes in isolation. The `git branch` command is used to manage branches.
git branch feature-branch(creates a new branch named “feature-branch”)git checkout feature-branch(switches to the “feature-branch”)git merge feature-branch(merges the “feature-branch” into the current branch, typically the main branch) - Cloning a Repository: If you are working on a project that is already hosted on a remote repository, you can clone it to your local machine using the `git clone` command.
git clone [repository URL] - Pushing and Pulling Changes: After making changes, you can push them to a remote repository to share them with others. To get the latest changes from a remote repository, you can pull them.
git push origin main(pushes your local changes to the “main” branch of the remote repository)git pull origin main(pulls the latest changes from the “main” branch of the remote repository)
Benefits of Using Git for Collaboration and Code Management
Git provides significant advantages for collaboration and code management in back-end development, enhancing productivity and reducing the risk of errors.
- Improved Collaboration: Git facilitates concurrent development by allowing multiple developers to work on the same project simultaneously. Features like branching and merging enable seamless integration of code from different contributors.
- Reduced Risk of Errors: Version control allows developers to revert to previous working versions if a bug is introduced or a feature breaks the application. This rollback capability minimizes the impact of errors.
- Code History and Auditing: Git maintains a detailed history of code changes, including who made the changes, when, and why. This history is invaluable for understanding the evolution of the project and for auditing purposes.
- Simplified Code Review: Git makes code review easier by providing tools for comparing changes and identifying potential issues. This process helps to improve code quality and reduce the likelihood of bugs.
- Increased Productivity: By streamlining collaboration and providing tools for managing code changes, Git helps developers work more efficiently. Features like branching and merging allow developers to experiment with new features without affecting the main codebase, accelerating the development process.
Deployment and Hosting
Deploying your back-end application is the crucial final step, making your hard work accessible to users. This involves taking your code and placing it on a server where it can run continuously, handling requests and serving responses. Choosing the right hosting environment and understanding the deployment process is essential for a smooth and reliable application.
The Deployment Process
Deploying a back-end application generally involves a series of steps, ensuring the application runs correctly on the server.
- Choosing a Hosting Provider: Select a provider that meets your application’s needs based on factors like scalability, cost, and supported technologies. Popular choices include cloud platforms like AWS, Google Cloud, and Azure, as well as dedicated server providers.
- Preparing the Application: This step includes packaging your code, dependencies, and configuration files. You might use tools like Docker to containerize your application, ensuring consistency across different environments.
- Setting Up the Server: Configure the server environment, which includes installing necessary software (like a web server such as Nginx or Apache, a database, and a runtime environment for your programming language) and setting up security measures.
- Deploying the Code: Transfer the application code to the server. This can be done manually via FTP, using a deployment tool, or through automated pipelines.
- Configuring the Application: Set up environment variables, database connections, and other necessary configurations for the application to run correctly in the production environment.
- Testing the Application: Thoroughly test the deployed application to ensure it functions as expected. This includes checking APIs, database interactions, and overall performance.
- Monitoring and Maintenance: Implement monitoring tools to track the application’s performance, identify errors, and ensure it remains available. Regularly update the application and server software to address security vulnerabilities and improve performance.
Hosting Options
Various hosting options cater to different needs, each with its own advantages and disadvantages.
Cloud Platforms: Cloud platforms like Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure offer a wide range of services and scalability options. They provide virtual machines, managed databases, load balancing, and other tools, allowing you to easily scale your application as demand increases.
- Advantages: High scalability, pay-as-you-go pricing, extensive services, global infrastructure.
- Disadvantages: Can be complex to manage, potential for vendor lock-in, cost can be unpredictable.
Dedicated Servers: Dedicated servers provide you with exclusive access to a physical server. This offers more control and performance, but requires more technical expertise to manage.
- Advantages: High performance, full control, predictable costs.
- Disadvantages: Requires more technical expertise, limited scalability, higher upfront costs.
Other Options: Other options include:
- Virtual Private Servers (VPS): VPSs offer a balance between dedicated servers and cloud platforms, providing virtualized resources on a physical server.
- Platform-as-a-Service (PaaS): PaaS platforms, such as Heroku or Google App Engine, simplify deployment by managing the underlying infrastructure, allowing you to focus on your code.
Setting Up a Basic Web Server and Deploying a Simple Application
Deploying a simple “Hello, World!” application on a basic web server demonstrates the fundamental steps involved. Let’s consider an example using Node.js and a simple server setup using Nginx.
Prerequisites: You’ll need a server (virtual or physical), SSH access to the server, and Node.js installed.
- Install Nginx: On your server, install Nginx using your operating system’s package manager (e.g., `sudo apt-get install nginx` on Ubuntu).
- Create a Simple Node.js Application: Create a file named `server.js` with the following content:
const http = require('http');
const hostname = '0.0.0.0'; // Listen on all interfaces
const port = 3000;
const server = http.createServer((req, res) =>
res.statusCode = 200;
res.setHeader('Content-Type', 'text/plain');
res.end('Hello, World!\n');
);
server.listen(port, hostname, () =>
console.log(`Server running at http://$hostname:$port/`);
);
- Upload the Application: Use an FTP client or `scp` to upload `server.js` to a directory on your server (e.g., `/var/www/my-app`).
- Configure Nginx: Create a configuration file for your application in the Nginx configuration directory (e.g., `/etc/nginx/sites-available/my-app`). The file should contain the following, adjusting the `server_name` and `proxy_pass` as needed:
server
listen 80;
server_name your_domain.com; # Replace with your domain or server IP
location /
proxy_pass http://localhost:3000; # Forward requests to your Node.js app
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
- Enable the Nginx Configuration: Create a symbolic link from the configuration file in `sites-available` to `sites-enabled` (e.g., `sudo ln -s /etc/nginx/sites-available/my-app /etc/nginx/sites-enabled/`).
- Start the Node.js Application: In the `/var/www/my-app` directory, run the Node.js application using `node server.js`. You might want to use a process manager like `pm2` to keep the application running in the background.
- Restart Nginx: Reload Nginx to apply the configuration changes (e.g., `sudo nginx -s reload`).
- Access the Application: Open your web browser and go to your server’s IP address or domain name. You should see “Hello, World!”.
This example provides a simplified view. Real-world deployments often involve more complex configurations, including database connections, environment variable management, and security measures. However, it demonstrates the basic principles of deploying a back-end application and serving it via a web server.
Security Considerations
Security is paramount in back-end development. Protecting user data and ensuring the integrity of your application are critical responsibilities. Neglecting security can lead to data breaches, reputational damage, and legal repercussions. This section delves into common vulnerabilities and best practices for building secure back-end systems.
Common Security Vulnerabilities
Back-end systems are susceptible to various security threats. Understanding these vulnerabilities is the first step toward mitigating them.
- SQL Injection: This vulnerability occurs when an attacker injects malicious SQL code into an input field, which is then executed by the database. This can allow the attacker to access, modify, or delete data in the database.
For example, consider a login form that uses the following SQL query:
SELECT
- FROM users WHERE username = '$username' AND password = '$password';If an attacker enters ‘ OR ‘1’=’1 as the username and password, the query becomes:
SELECT
- FROM users WHERE username = '' OR '1'='1' AND password = '';This modified query would bypass the authentication and allow the attacker to log in.
- Cross-Site Scripting (XSS): XSS vulnerabilities arise when an attacker injects malicious scripts (usually JavaScript) into a website that is then executed by other users’ browsers. This can lead to the theft of user credentials, session hijacking, or defacement of the website.
There are three main types of XSS:
- Stored XSS: The malicious script is permanently stored on the server (e.g., in a database). When a user visits a page containing the script, it’s executed.
- Reflected XSS: The malicious script is part of a request sent to the server (e.g., in a URL parameter). The server reflects the script back to the user, who then executes it.
- DOM-based XSS: The malicious script modifies the DOM (Document Object Model) in the user’s browser. The script is executed locally in the user’s browser.
- Cross-Site Request Forgery (CSRF): CSRF attacks trick a user into submitting a malicious request to a website where they are currently authenticated. This can lead to unauthorized actions being performed on the user’s behalf.
For example, an attacker could craft a hidden form that, when submitted by the user, transfers money from their account to the attacker’s account.The user is unaware that they are submitting this form.
- Broken Authentication and Session Management: Weaknesses in authentication and session management mechanisms can allow attackers to gain unauthorized access to user accounts. This includes weak password policies, lack of multi-factor authentication, and insecure session handling.
- Security Misconfiguration: This refers to errors in the configuration of servers, databases, and other components of the back-end system. These errors can leave the system vulnerable to attack. Examples include:
- Default credentials not changed.
- Unnecessary services enabled.
- Verbose error messages that reveal sensitive information.
- Insecure Direct Object References: This occurs when an application exposes direct references to internal implementation objects, such as files, directories, or database keys. An attacker can manipulate these references to access unauthorized data.
- Sensitive Data Exposure: This involves the improper handling of sensitive data, such as passwords, credit card numbers, and personal information. This can result in data breaches and privacy violations.
- Using Components with Known Vulnerabilities: This occurs when developers use outdated or vulnerable libraries, frameworks, or other software components. Attackers can exploit known vulnerabilities in these components to compromise the system.
Securing User Data and Preventing Unauthorized Access
Protecting user data and preventing unauthorized access is essential for maintaining the integrity and trustworthiness of a back-end application. Implementing robust security measures is crucial.
- Input Validation and Sanitization: Always validate and sanitize user input to prevent SQL injection, XSS, and other injection attacks.
- Input Validation: Ensure that the input conforms to the expected format and data type. For example, validate that a username only contains alphanumeric characters and is of a certain length.
- Input Sanitization: Remove or encode potentially harmful characters from the input. For example, escape special characters in SQL queries to prevent SQL injection.
- Authentication and Authorization: Implement strong authentication and authorization mechanisms to verify user identities and control access to resources.
- Authentication: Verify the user’s identity (e.g., using a username and password).
- Authorization: Determine what resources the authenticated user is allowed to access.
- Data Encryption: Encrypt sensitive data both in transit (using HTTPS/TLS) and at rest (e.g., using AES encryption for database fields).
For example, encrypting passwords before storing them in the database. Never store passwords in plain text. - Regular Security Audits and Penetration Testing: Regularly audit your code and perform penetration testing to identify and address security vulnerabilities.
Consider using automated security scanners and manual code reviews. - Use a Web Application Firewall (WAF): A WAF can help to protect your application from common web attacks, such as SQL injection and XSS.
- Keep Software Updated: Regularly update all software components (e.g., operating systems, web servers, databases, libraries) to patch known vulnerabilities.
- Implement the Principle of Least Privilege: Grant users only the minimum necessary permissions to perform their tasks. This limits the impact of a potential security breach.
- Secure Session Management: Implement secure session management practices, such as:
- Generating strong session IDs.
- Using HTTPS to transmit session cookies.
- Setting session expiration times.
- Invalidating sessions after a user logs out or a period of inactivity.
Designing a Secure Authentication System
A secure authentication system is crucial for protecting user accounts and data. Implementing best practices is essential.
- Password Storage:
- Hashing: Store passwords as securely hashed values, using a strong hashing algorithm like bcrypt or Argon2. Never store passwords in plain text.
- Salting: Use a unique salt for each password to prevent rainbow table attacks. The salt should be randomly generated and stored alongside the hashed password.
- Password Strength Policies: Enforce strong password policies, such as requiring a minimum length, a mix of character types, and regular password changes.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security. This requires users to provide a second factor of authentication, such as a code from an authenticator app or a one-time password (OTP) sent to their email or phone.
- Rate Limiting: Implement rate limiting to prevent brute-force attacks. Limit the number of login attempts allowed from a specific IP address or user account within a given time period.
- Account Lockout: Lock user accounts after a certain number of failed login attempts. This makes it more difficult for attackers to guess passwords.
- Secure Session Management:
- Session ID Generation: Generate strong, unpredictable session IDs.
- Session Cookie Security: Set the `HttpOnly` and `Secure` flags on session cookies to prevent XSS attacks and ensure the cookie is only transmitted over HTTPS.
- Session Expiration: Set appropriate session expiration times, and invalidate sessions when users log out or after a period of inactivity.
- Two-Factor Authentication (2FA) Recovery: Provide users with a method to recover their accounts if they lose access to their 2FA device (e.g., a recovery code or a backup email address). Ensure that the recovery process is secure.
- Regular Security Updates: Keep your authentication system and related libraries up to date with the latest security patches.
- Example of a Secure Password Storage (using bcrypt):
In PHP, you can use the `password_hash()` function to hash a password using bcrypt:
$password = "mySecretPassword";
$hashed_password = password_hash($password, PASSWORD_BCRYPT);To verify the password:
if (password_verify($password, $hashed_password))
// Password is correct
else
// Password is incorrect
Testing and Debugging

Testing and debugging are crucial components of back-end development, ensuring the reliability, stability, and functionality of your applications. Writing tests allows you to verify that your code behaves as expected, catching errors early in the development cycle. Debugging, on the other hand, is the process of identifying and resolving errors that arise during testing or in production. Together, testing and debugging contribute to building robust and maintainable back-end systems.
The Importance of Testing Back-End Code
Testing is an essential practice in back-end development because it helps to identify and fix bugs before they reach production, which can save time, money, and resources. Thorough testing leads to more reliable software, improving user experience and reducing the likelihood of system failures. Testing also serves as documentation, clarifying the intended behavior of the code.There are two main types of tests commonly used in back-end development: unit tests and integration tests.
- Unit Tests: Unit tests focus on testing individual components or units of code in isolation. They verify that each function, method, or class works correctly on its own. Unit tests are typically small, fast, and easy to write. They help developers ensure that each piece of code functions as designed. For example, a unit test might verify that a function correctly calculates the sum of two numbers.
- Integration Tests: Integration tests verify that different components or modules of your code work together correctly. They test the interactions between different parts of the system, such as the interaction between a database and an API endpoint. Integration tests are generally more complex than unit tests, as they involve testing multiple components simultaneously. They help developers ensure that the different parts of the system integrate seamlessly.
For example, an integration test might verify that an API endpoint correctly retrieves data from a database and returns it in the expected format.
Debugging Techniques for Identifying and Resolving Errors
Debugging involves identifying the root cause of an error and fixing it. Effective debugging skills are essential for back-end developers to ensure that their code functions correctly. Several techniques can be used to identify and resolve errors.
- Reading Error Messages: Error messages provide valuable information about what went wrong and where. Carefully read the error messages, paying attention to the file name, line number, and error type. This information can often lead you directly to the source of the problem. For instance, a “TypeError: ‘NoneType’ object is not iterable” error indicates that you’re trying to iterate over a variable that is None, which is not allowed.
- Using Logging: Logging involves inserting print statements or logging statements throughout your code to track the execution flow and the values of variables. This can help you understand how your code is behaving and identify where errors are occurring. You can use different log levels (e.g., DEBUG, INFO, WARNING, ERROR) to categorize log messages based on their severity. For example, you could log the value of a variable before and after a calculation to see if the calculation is producing the expected result.
- Using Debuggers: Debuggers are tools that allow you to step through your code line by line, inspect variables, and set breakpoints. This gives you fine-grained control over the execution of your code and helps you pinpoint the exact location of an error. Most modern IDEs (Integrated Development Environments) have built-in debuggers.
- Rubber Duck Debugging: Explain your code to an inanimate object, such as a rubber duck. The act of explaining your code often helps you identify errors or misunderstandings. By verbalizing your code and its logic, you may discover the issue yourself.
- Code Review: Having another developer review your code can help you identify errors that you might have missed. A fresh pair of eyes can often spot problems that you’re too close to see.
Demonstrating Debugging Tools in Python
Python has a built-in debugger called `pdb` (Python Debugger), which can be used to step through your code, inspect variables, and set breakpoints. Most modern IDEs, such as VS Code, PyCharm, and others, provide graphical interfaces for the debugger, making it easier to use.Here’s how to use the `pdb` debugger in Python:
1. Import the `pdb` module
At the top of your Python file, import the `pdb` module: `import pdb`.
2. Set a breakpoint
Insert the line `pdb.set_trace()` in your code where you want the debugger to start. This line will pause the execution of your program and enter the debugger.
3. Run your code
Execute your Python script. When the interpreter reaches the `pdb.set_trace()` line, it will stop and give you a `(Pdb)` prompt.
4. Use debugger commands
At the `(Pdb)` prompt, you can use various commands to debug your code. Some of the most common commands are:
- `n` (next): Executes the next line of code.
- `s` (step): Steps into a function call.
- `c` (continue): Continues execution until the next breakpoint or the end of the program.
- `p` (print): Prints the value of a variable (e.g., `p variable_name`).
- `q` (quit): Exits the debugger and the program.
- `l` (list): Lists the current code context.
5. Example
“`python import pdb def add_numbers(a, b): pdb.set_trace() # Breakpoint result = a + b return result x = 5 y = 10 sum_result = add_numbers(x, y) print(f”The sum is: sum_result”) “` When you run this code, the debugger will stop at the `pdb.set_trace()` line.
You can then use the debugger commands to step through the code, inspect the values of `a`, `b`, and `result`, and understand the execution flow.
Scaling and Performance

Scaling and performance are critical aspects of back-end development, especially as applications grow in popularity and user base. The ability to handle increased traffic, data volume, and complex operations efficiently directly impacts user experience and the overall success of a back-end system. Understanding how to optimize performance and scale applications is essential for building robust and reliable back-end solutions.
Strategies for Scaling Back-End Applications
Scaling back-end applications involves adjusting resources to accommodate increased demand. This can be achieved through several strategies, often implemented in combination.
- Vertical Scaling: This involves increasing the resources of a single server, such as CPU, RAM, or storage. While straightforward, it has limitations as hardware has physical limits. For example, if a database server is experiencing slow query performance, vertical scaling might involve upgrading the server’s RAM to allow for more data to be cached in memory, thus speeding up query execution.
However, there is a limit to how much RAM a single server can support.
- Horizontal Scaling: This approach involves adding more servers to the system. This is generally more scalable than vertical scaling, as it allows for virtually unlimited growth. Consider a web application that initially runs on one server. As the number of users increases, more servers can be added to handle the load. A load balancer distributes incoming requests across these servers, ensuring no single server is overwhelmed.
- Load Balancing: Distributes incoming network traffic across multiple servers. This improves resource utilization, prevents overload, and enhances application availability. Load balancers can use different algorithms (e.g., round robin, least connections) to distribute traffic. For instance, a load balancer might distribute user requests evenly across three web servers, ensuring each server handles roughly the same amount of traffic.
- Caching: Stores frequently accessed data in a faster storage medium (e.g., RAM or a dedicated cache server) to reduce the load on the main data source (e.g., a database). Caching strategies are discussed in detail in the next .
- Database Optimization: Optimizing database queries, indexing, and schema design is crucial for performance. This can involve rewriting inefficient queries, adding indexes to frequently queried columns, and optimizing the database schema to reduce data redundancy. For example, adding an index to the ‘customer_id’ column in a ‘orders’ table can significantly speed up queries that filter by customer ID.
- Asynchronous Tasks: Offloading time-consuming tasks (e.g., sending emails, processing large files) to background processes can prevent blocking the main application thread, improving responsiveness. Message queues like RabbitMQ or Kafka are often used to manage these tasks. For example, instead of sending an email directly to a user after they register (which can take several seconds), the application can add a message to a queue.
A separate worker process then picks up the message and sends the email asynchronously.
- Microservices Architecture: Breaking down a monolithic application into smaller, independent services can improve scalability and maintainability. Each microservice can be scaled independently based on its specific needs. For instance, an e-commerce application might be broken down into services for product catalog, user accounts, shopping cart, and order processing. Each service can be scaled independently, for example, the order processing service can be scaled up during peak sales periods.
- Content Delivery Networks (CDNs): CDNs store cached content (e.g., images, videos, and static files) on servers geographically distributed across the world. This reduces latency for users accessing content from different locations. For example, a website with a large global audience can use a CDN to store images and videos on servers located near users in various countries. This results in faster loading times for users worldwide.
Caching Mechanisms to Improve Performance
Caching is a crucial technique for improving the performance of back-end applications. By storing frequently accessed data in a faster, more accessible location, caching reduces the load on slower data sources, such as databases or external APIs. Different caching mechanisms can be used depending on the specific needs of the application.
- Browser Caching: Web browsers cache static resources like images, CSS files, and JavaScript files. This reduces the number of requests to the server and speeds up page load times for returning visitors. The server sets HTTP headers (e.g., `Cache-Control`, `Expires`) to control how long the browser should cache these resources.
- Server-Side Caching: Server-side caching involves caching data on the server itself. This can be implemented in various ways:
- In-Memory Caching: Data is stored in the server’s RAM, providing very fast access times. Popular in-memory caching solutions include Redis and Memcached. These are suitable for frequently accessed data that changes relatively infrequently.
- Caching at the Database Level: Databases often have built-in caching mechanisms. Query results can be cached to reduce the load on the database server.
- Object Caching: Caching the results of complex computations or database queries to reduce the load on the CPU and the database. For example, caching the results of a complex calculation used to generate a report.
- CDN Caching: CDNs cache static content (e.g., images, videos, and JavaScript files) on servers located geographically closer to users. This reduces latency and improves loading times.
- Reverse Proxy Caching: A reverse proxy server (e.g., Nginx or Varnish) sits in front of the web server and caches responses from the origin server. This reduces the load on the origin server and improves performance. The reverse proxy can cache static and dynamic content, and it can also handle tasks like SSL termination and load balancing.
- Cache Invalidation Strategies: It’s important to have strategies for invalidating cached data when the underlying data changes. Common strategies include:
- Time-Based Expiration: Cached data expires after a set time period. This is simple to implement but can lead to stale data if the underlying data changes before the expiration time.
- Cache Tags/Keys: Assigning tags or keys to cached data allows for selective invalidation when related data changes.
- Event-Driven Invalidation: The cache is invalidated based on events, such as database updates or API calls.
Identifying Bottlenecks and Optimization Techniques
Identifying bottlenecks in a back-end application is crucial for performance optimization. This involves analyzing the application’s behavior to pinpoint areas where performance is slow or inefficient. Several tools and techniques can be used to identify and address these bottlenecks.
- Profiling: Profiling tools (e.g., `py-spy` for Python, `perf` for Linux) can be used to analyze the application’s performance and identify which parts of the code are taking the most time. Profilers provide detailed information about function calls, execution times, and memory usage. For example, profiling a Python application might reveal that a specific function is spending a significant amount of time performing database queries.
- Monitoring: Monitoring tools (e.g., Prometheus, Grafana, Datadog) collect metrics about the application’s performance, such as CPU usage, memory usage, response times, and database query times. These metrics can be visualized in dashboards to identify trends and anomalies. For example, monitoring might reveal that the application’s response times are increasing during peak hours, indicating a potential performance bottleneck.
- Load Testing: Load testing tools (e.g., JMeter, Locust, Gatling) simulate multiple users accessing the application simultaneously to assess its performance under load. Load testing helps identify bottlenecks, such as slow database queries or inefficient code, that might not be apparent under normal traffic conditions. For example, load testing might reveal that the application’s database server is overloaded when handling a large number of concurrent requests.
- Database Query Optimization: Slow database queries are a common source of performance bottlenecks. Optimization techniques include:
- Query Analysis: Analyze slow queries using database-specific tools (e.g., `EXPLAIN` in MySQL) to understand how the database is executing the query and identify areas for improvement.
- Indexing: Add indexes to frequently queried columns to speed up query execution.
- Query Rewriting: Rewrite inefficient queries to improve performance.
- Code Optimization: Identifying and optimizing inefficient code is crucial for performance. This can involve:
- Algorithm Optimization: Improving the efficiency of algorithms used in the application.
- Code Review: Reviewing code for potential performance issues, such as inefficient loops or excessive object creation.
- Caching: Implementing caching to reduce the load on the database and other resources.
- Resource Optimization: Optimizing the use of system resources (CPU, memory, disk I/O) is important for performance. This can involve:
- Resource Allocation: Ensuring that the application has sufficient resources to handle the load.
- Memory Management: Optimizing memory usage to prevent memory leaks and reduce garbage collection overhead.
- Disk I/O Optimization: Reducing the number of disk I/O operations to improve performance.
- Example Scenario: Consider an e-commerce application where users are experiencing slow loading times when viewing product pages. Profiling might reveal that a specific function responsible for fetching product details from the database is taking a significant amount of time. Further investigation using the database’s `EXPLAIN` tool reveals that the query used by this function is inefficient and lacks appropriate indexes. The solution would involve adding indexes to the relevant columns in the database and rewriting the query to optimize its performance.
Conclusive Thoughts
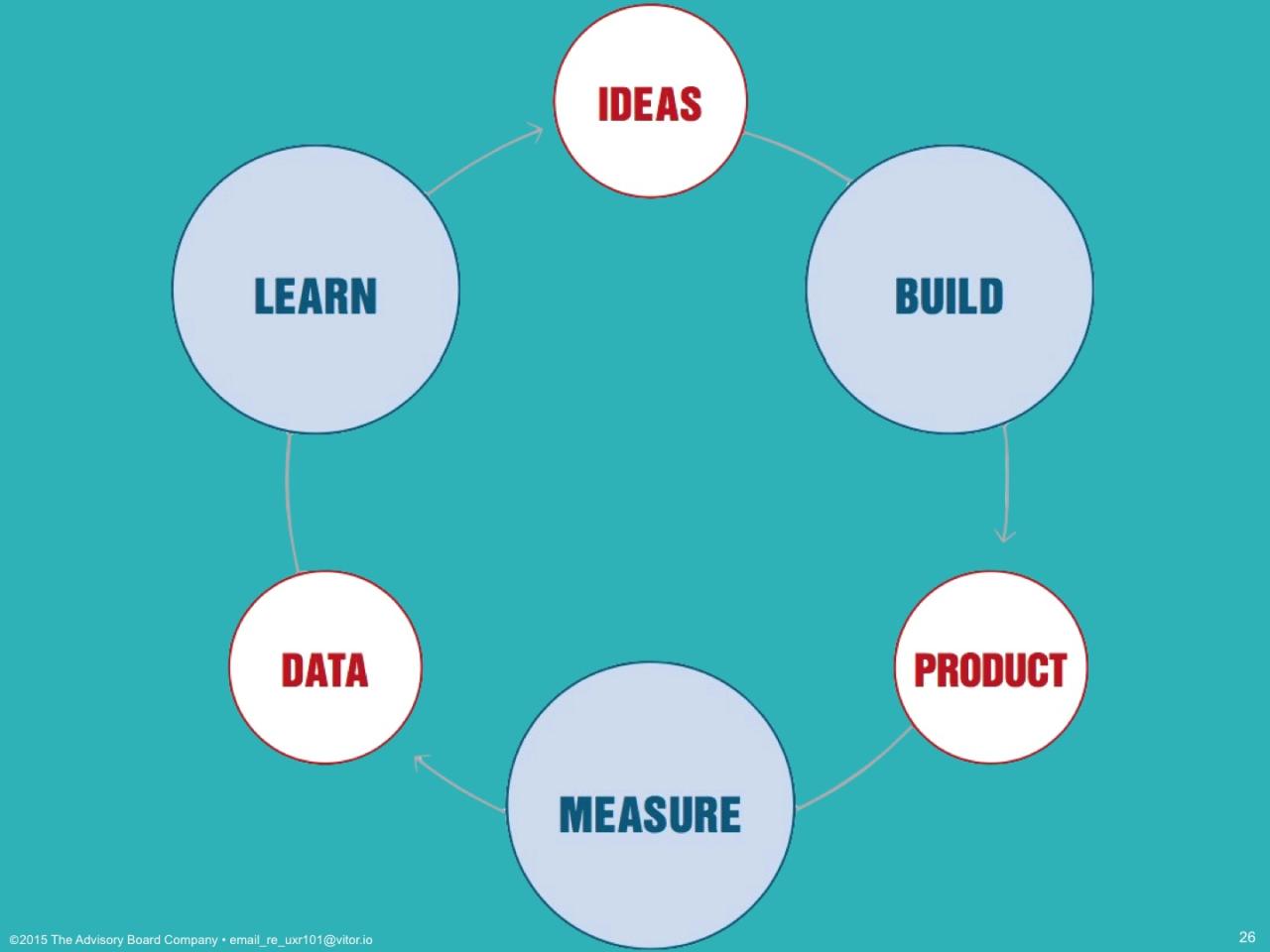
In conclusion, understanding back-end development is like learning the secret language that makes the digital world function. We’ve traversed the essential concepts, from the underlying technologies to the crucial aspects of security and scalability. By grasping these basics, you’re not just understanding a technical field; you’re gaining insights into how the internet works and the ability to build powerful, functional applications.
Embrace this knowledge, and continue exploring – the world of back-end development is vast and ever-evolving, offering endless opportunities for learning and innovation.